SSH
SSH (Secure Shell)
SSH is a program that enables secure logins over an insecure network. It encrypts all the data passing both ways so that it cannot be read if it is intercepted. It also replaces old and insecure tools like telnet, rlogin, rcp, FTP, etc. SSH is a client-server software. Both machines must have ssh installed for it to work.
We have already installed a ssh server on our machines, and you must have installed an ssh client on your local machine. SSH is available without charge for almost all versions of UNIX (including Linux and MacOS X). For UNIX and derivatives, we recommend using the OpenSSH client, downloadable from http://www.openssh.org, and for Windows users, we recommend using PuTTy, a free ssh client that can be downloaded from http://www.putty.org.
Otherwise, any client compatible with SSH version 2 can be used. If you want to try a more straightforward client with multi-tab capabilities, we recommend using Solar-PuTTY.
Linux (OpenSSH)
Generating an SSH key pair
To generate an SSH key pair, you can run the following command:
ssh-keygen
You will be prompted to accept your private key's default name and location, but you can choose another location/name at your convenience:
Enter file in which to save the key (/home/<username>/.ssh/id_rsa):
By default, keys are stored in the local machine's ~/.ssh/ directory.
Remember that if you create your SSH keys using a different name or location than the defaults, then you'll need to explicitly point to your private key when you run your ssh login command:
ssh -i /path/to/my/private-key -l <username> <servername>
The following two steps are regarding passphrase; creating your private key without one is possible:
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
In the end, you should have an output similar to this:
Your identification has been saved in /home/<username>/.ssh/id_rsa.
Your public key has been saved in /home/<username>/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:uL2hmj/FugVUKW/jvXewAPRupmUkEVzLiJXLX6DHdXk user@support
The key's randomart image is:
+---[RSA 2048]----+
| .+=. . |
| .+*o... o E|
| o=.*oo . . |
| . .X = . |
| o+SX . |
| ++ X . |
| .o+* o o |
| .oo.o. o . |
| oo+o. . . |
+----[SHA256]-----+
Also, the ssh-keygen command allows you to do something like this:
#For example, to add a comment saying
#which user created the key
#on which machine and when
ssh-keygen -C "$(whoami)@$(uname -n)-$(date -I)"
Copying the public key to the GPFS (remote server)
So that you can authenticate using your SSH keys, the public key
must be added to the remote server ~/.ssh/authorized_keys file.
The public key file shares the same name as the private key but adds the suffix .pub.
If your public key is ~/.ssh/id_rsa.pub (the default public key file location/name), just do the following:
ssh-copy-id <username>@transfer1.bsc.es
Otherwise, you must explicitly provide the path of your public key:
ssh-copy-id -i ~/.ssh/mykey.pub <username>@transfer1.bsc.es
Ensure that your ~/.ssh directory in the GPFS has the write permissions for 'group'
(g) and 'other' (o) disabled; otherwise, SSH authentication will not work, and you will be
prompted for the password anyway.
Never share your private key; it has to remain on your local machine.
Creating a config file for Linux
In Linux-based systems, a config file can be created to make the login process into a machine faster. If properly configured, there is no need to specify the username, and an alias can be used for each machine.
First of all, create the config file as shown below:
vim ~/.ssh/config
Once editing it, you can specify multiple aliases for each host you want. An example for the MareNostrum5 logins would be:
Host gpp gpp1 glogin1 glogin1.bsc.es
HostName glogin1.bsc.es
User <your-username>
Host gpp2 glogin22 glogin2.bsc.es
HostName glogin2.bsc.es
User <your-username>
Host acc acc1 alogin1 alogin1.bsc.es
HostName alogin1.bsc.es
User <your-username>
If your SSH Keys are set up correctly, you should be able to access the 'glogin1' of MareNostrum5 (glogin1.bsc.es), for example, by simply executing any of the following commands:
ssh glogin1
ssh gpp
ssh gpp1
ssh glogin1.bsc.es
Options you use in an SSH command can also be specified in your config file:
#ssh command:
ssh gpp1 -o ForwardX11=true
#~/.ssh/config file:
Host gpp gpp1 glogin1 glogin1.bsc.es
HostName glogin1.bsc.es
User <your-username>
ForwardX11 true
Known issue when accessing too-old machines
Chances are if you've installed a newer version of the ssh client, you could get an error when accessing an old machine like the BSC's cluster MinoTauro:
Unable to negotiate with <your IP> port 22: no matching host key type found. Their offer: ssh-rsa,ssh-dss
Then you might need to add some options to your ssh command, for example:
ssh -o HostKeyAlgorithms=+ssh-rsa -o PubkeyAcceptedKeyTypes=+ssh-rsa <username>@mt1.bsc.es
Or in the ~/.ssh/config file:
Host mt mt1 mt1.bsc.es
HostName mt1.bsc.es
User <your-username>
HostKeyAlgorithms +ssh-rsa
PubkeyAcceptedKeyTypes +ssh-rsa
Windows (PuTTy)
This section describes installing, configuring and using PuTTy on Windows machines, as it is the most known Windows SSH client. No matter your client, you will need to specify the following information:
- Select SSH as default protocol
- Select port 22
- Specify the remote machine and username
For example with putty client:

This is the first window that you will see at putty startup. Once finished, press the Open button. If it is your first connection to the machine, your will get a Warning telling you that the host key from the server is unknown, and will ask you if you are agree to cache the new host key, press Yes.
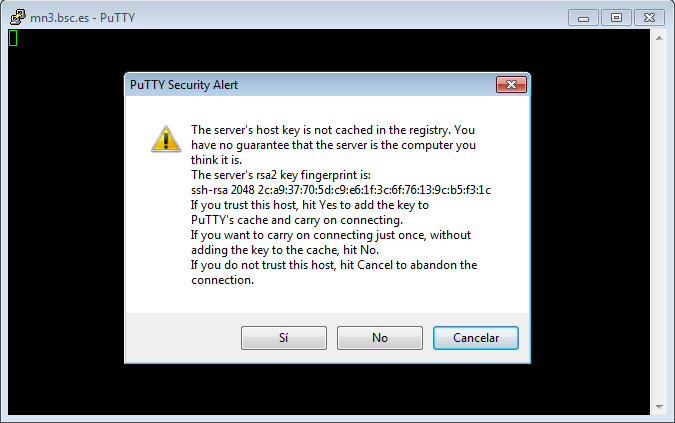
If you see this warning another time and you haven't modified or reinstalled the ssh client, please do not log in, and contact us as soon as possible (see Getting Help.
Finally, a new window will appear asking for your login and password:

Generating SSH keys with PuTTY
First of all, open PuTTY Key Generator. You should select Type RSA and 2048 or 4096 bits, then hit the "Generate" button.

After that, you will have to move the mouse pointer inside the blue rectangle, as in picture:

You will find and output similar to the following picture when completed

This is your public key, you can copy the text in the upper text box to the notepad and save the file. On the other hand, click on "Save private key" as in the previous picture, then export this file to your desired path.
You can close PuTTY Key Generator and open PuTTY by this time,
To use your recently saved private key go to Connection -> SSH -> Auth, click on Browse... and select the file.
